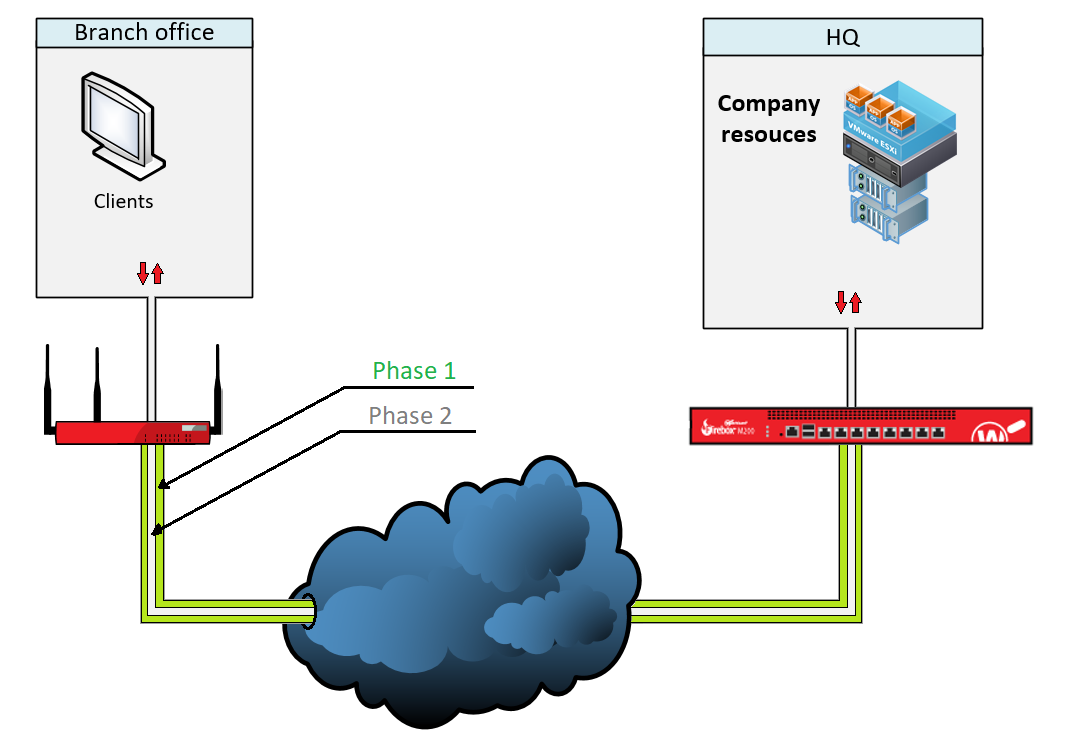
This article describles how to setup an IPsec VPN tunnel. An IPsec VPN Tunnel consists of two phases:
- Phase 1 is where the endpoints of the tunnel negotiate and set up a VPN Tunnel.
- Phase 2 is where the the networks on both private networks get connected to each other encrypted via ESP. Traffic for private Networks that is matching no explicit routes routes will be dropped.WARNING!! Be careful when adding new routes! There are some firewalls are so strict they will shut down the entire tunnel if traffic reaches them that they have no route for!
Before setting up the tunnel
Before the tunnel can be set up both sides have to be clear on a bunch of tecnical details about the tunnel. WARNING: Almost all issues in setting up the tunnel happen if therse parameters are not perfectly aligned.
General:
- Tunnel Endpoints
- Gateway IDs
- IKE version
- Authentication algorithm
- Encryption algorithm
- Diffie-hellmann-group
- Lifetime
- Encryption scheme
- Negotioation mode
- DPD traffic idle timeout
- DPD max retries
- IKE keep alive
- Encryption protocol
- Authentication algorithm
- Encryption algorithm
- Encapsulation Mode
- Perfect foreword security
- PFS group
- Key expiration time
- Key expiration traffic
Setting up the tunnel
At first we open the Branch Office Tunnels configuration.
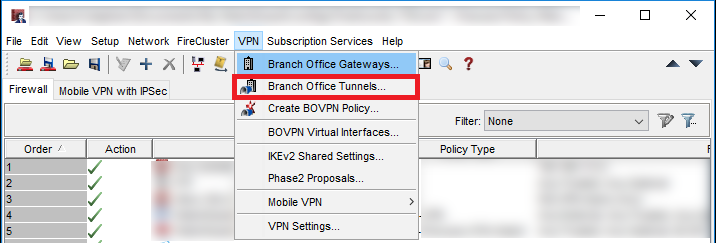
Here you add a new tunnel and define the Routes. These are the Routes of the networks beeing connected in Phase 2.
We add these by clicking Add… Here we add the Lokal and the Remote private networks in CIDR notation (i.e. /24). We can add more Routes later on.
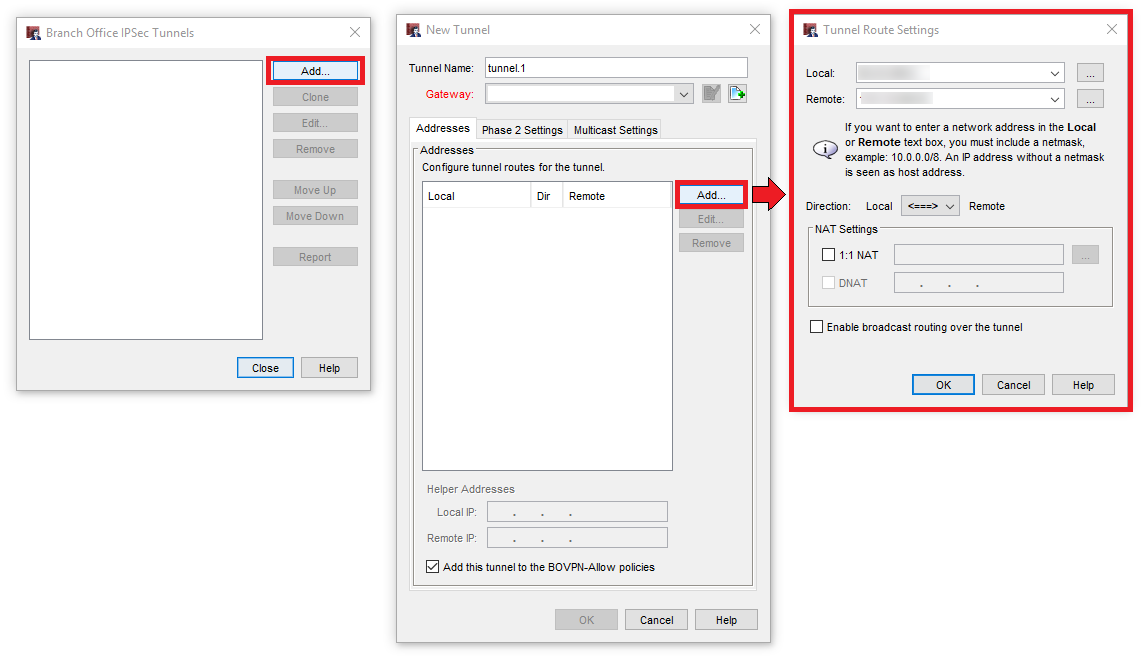
Afterwards we define a new gateway and enter the PSK.
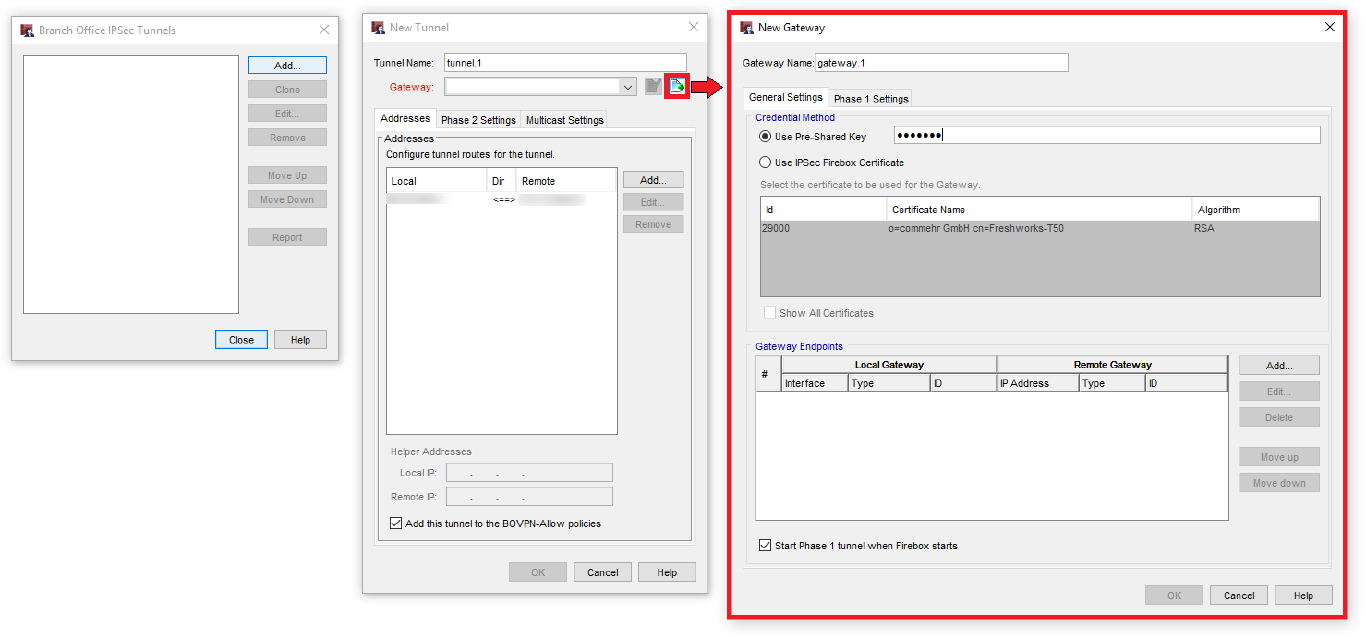
Now switch to the Phase 1 Settings and configure:
- IVEv version
- Mode
- Keep-alive Interval
- DPD Settings
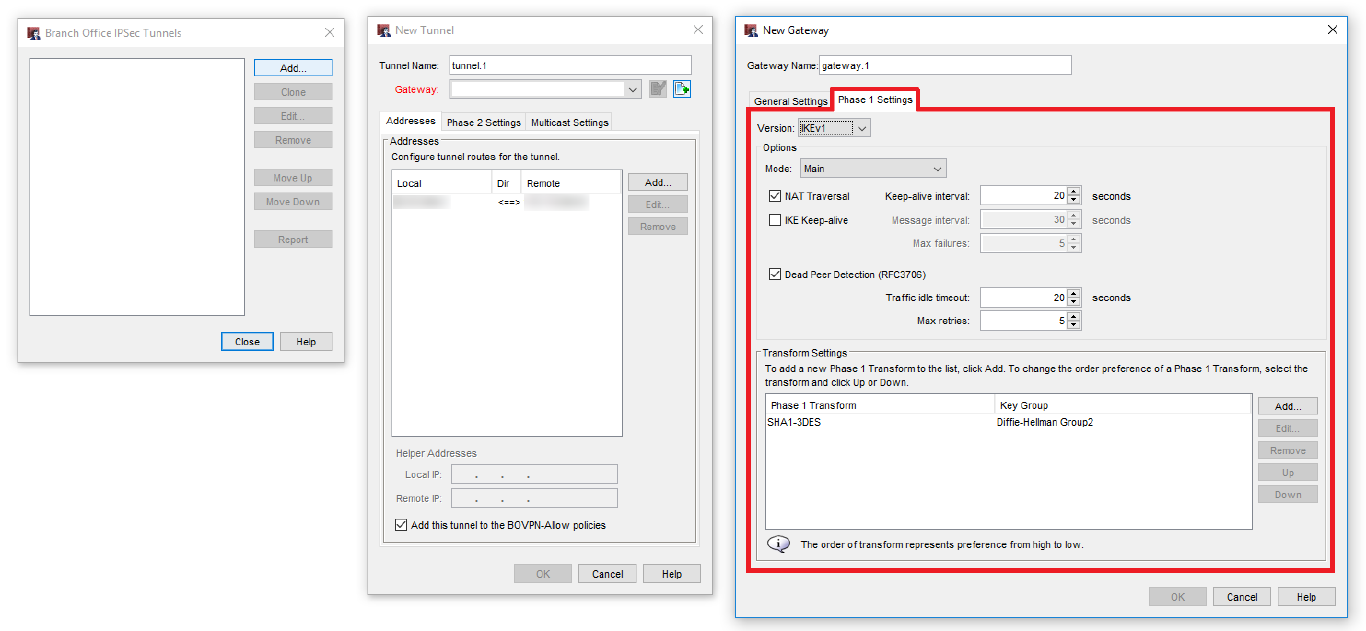
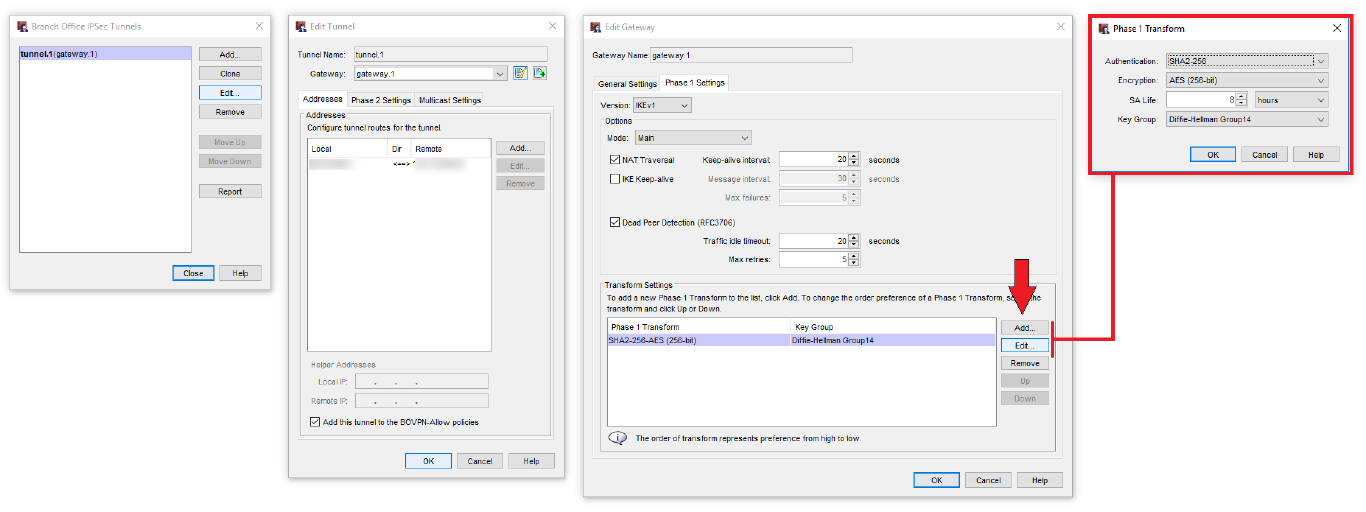
Then we configure the Transform Settings:
- Authentication algorithm
- Encryption algorithm
- SA Life
- Diffie-Hellmann group
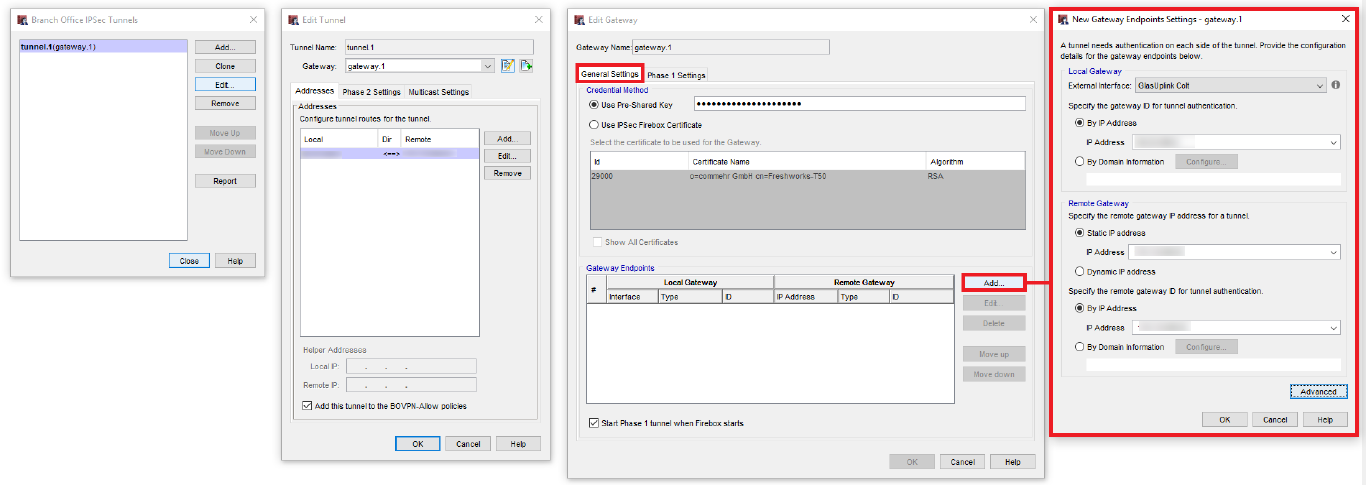
Now we go back to General Settings and define the tunnel endpoints (phase 1).
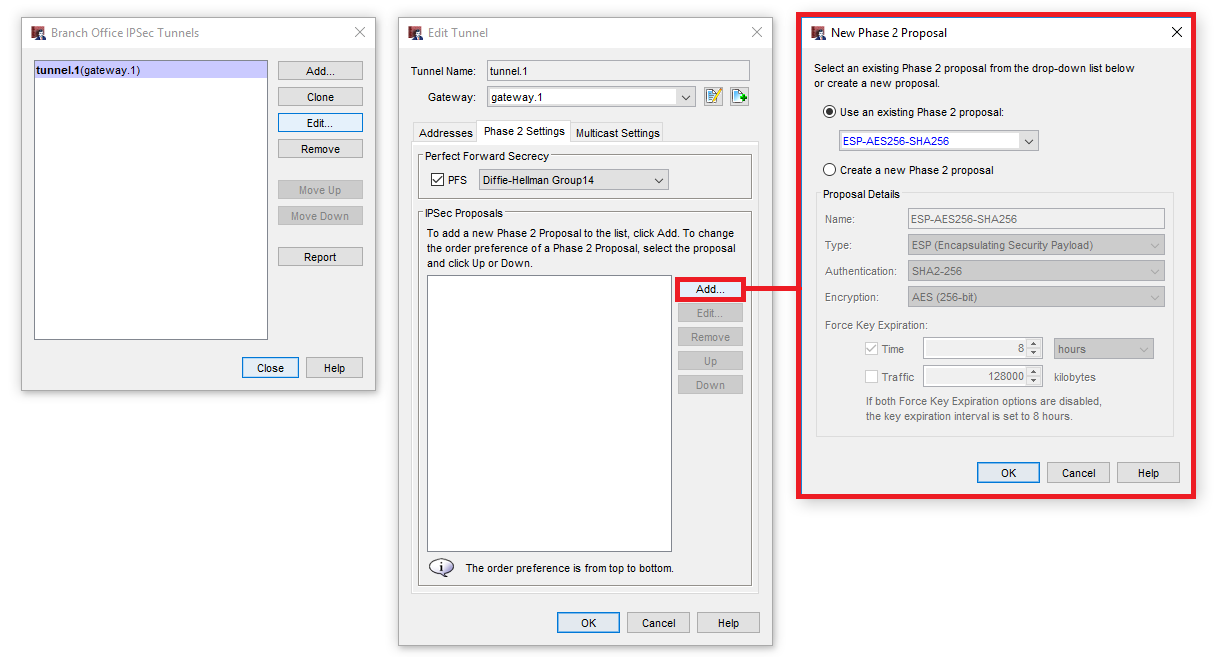
Now we switch to the Phase 2 Settings, activate Perfect Forward Security and define the Diffie-Hellman Group. Now we just have to configure the Phase 2 Proposal:
- Encryption protocol
- Authentication algorithm
- Encryption algorithm
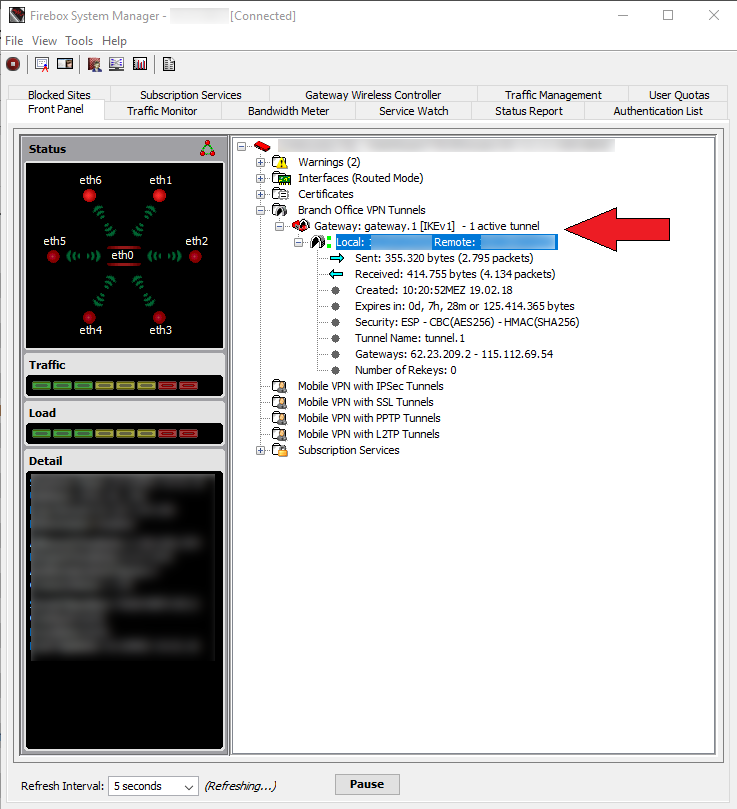
Check if the tunnel comes up
If both parties have the EXACT same Phase 1/2 parameters set up the tunnel should come online. It looks like this in the System Manager.
Cheers, Ori