In an active / passiv cluster, as the name suggests, one of the firewalls is active and the other one is passive. In case on of the firewalls fails the other one is taking over.
The following states of a cluster member are possible:
- Master: The currently active firewall
- Backup Master: The currently passive firewall
- Inactive: The firewall is unreachable
If the primary firewall fails, it is shown as inactive Inactive and the Backup Master becomes the Master.
If the failed firewall comes back online it becomes the Backup Master. A failback is not happening!
We define two interfaces on wich the firewalls are connected direclty to each other. These Interfaces are called „Cluster Interface“ and serve the following purposes:
- Make sure the configuration stays the same on both devices (DHCP Leases, Networks etc.)
- Decide who is active and who is passive
- Check if the other one is still alive
I suggest you are using two interfaces for that. The last thing you want is both firewalls becomming Master. This can happen if the firewalls can’t reach each other because of a failing cable or Interface. In this case you run into whats called a “Split Brain”, where the data on both Boxes are desynching and you have a double DHCP server, NTP server etc. in your network.
Setup
At first you should boot the Firewalls into Recovery Mode to make sure all configurtions are reset to default.


We connect to one of the firewalls via eth1 and start the Firecluster Wizard by going to Policy Manager > Firecluster > Setup.

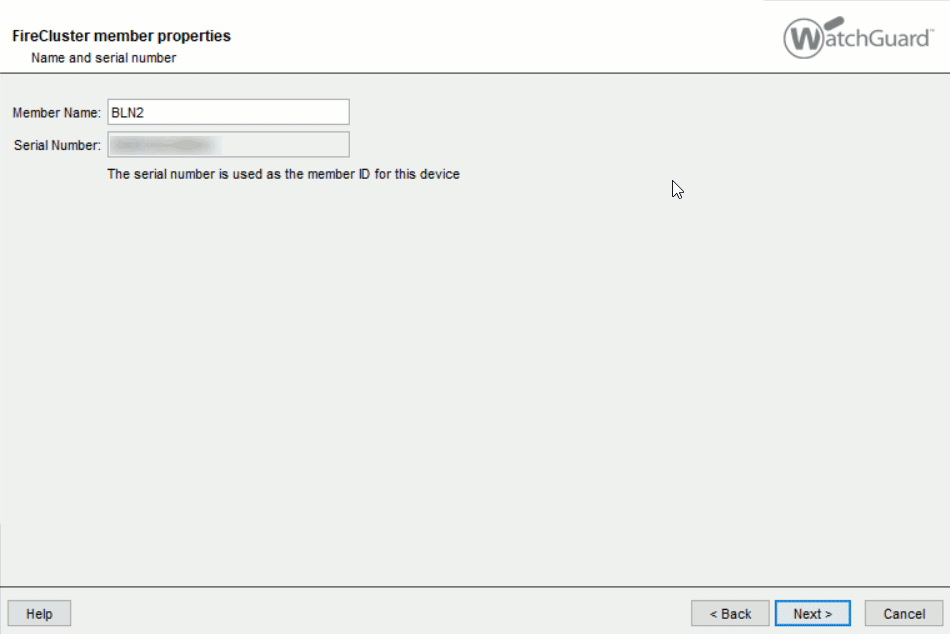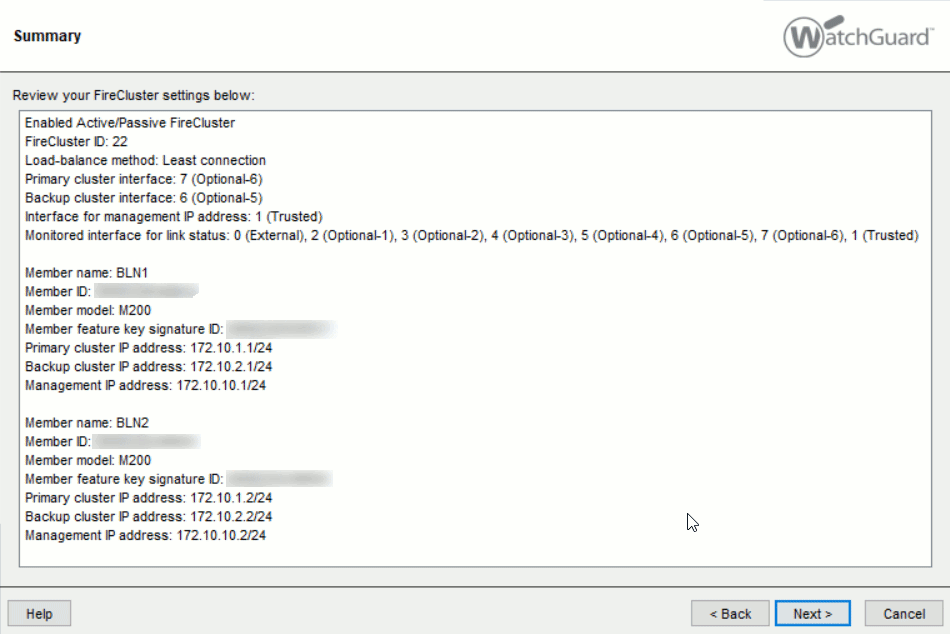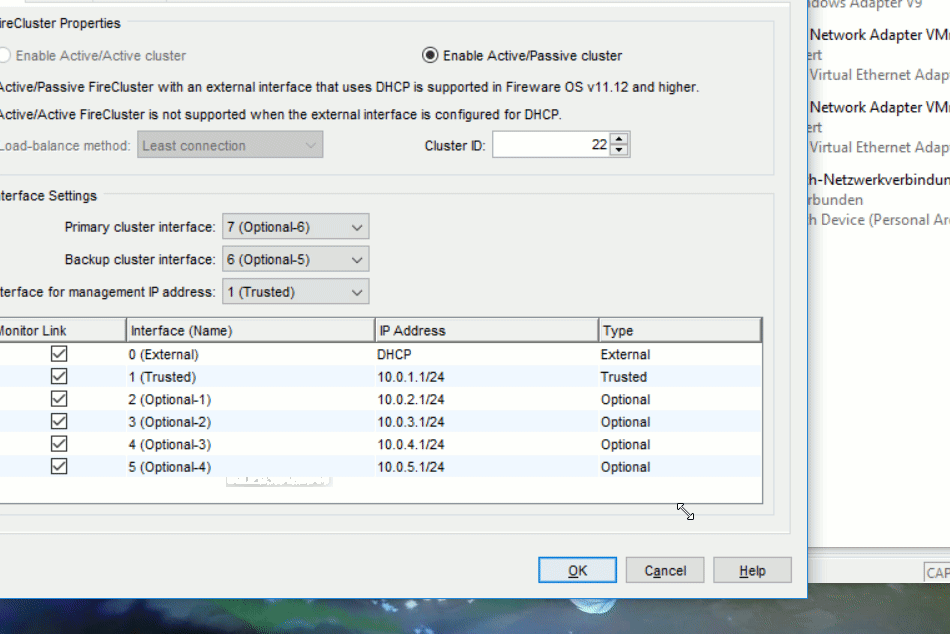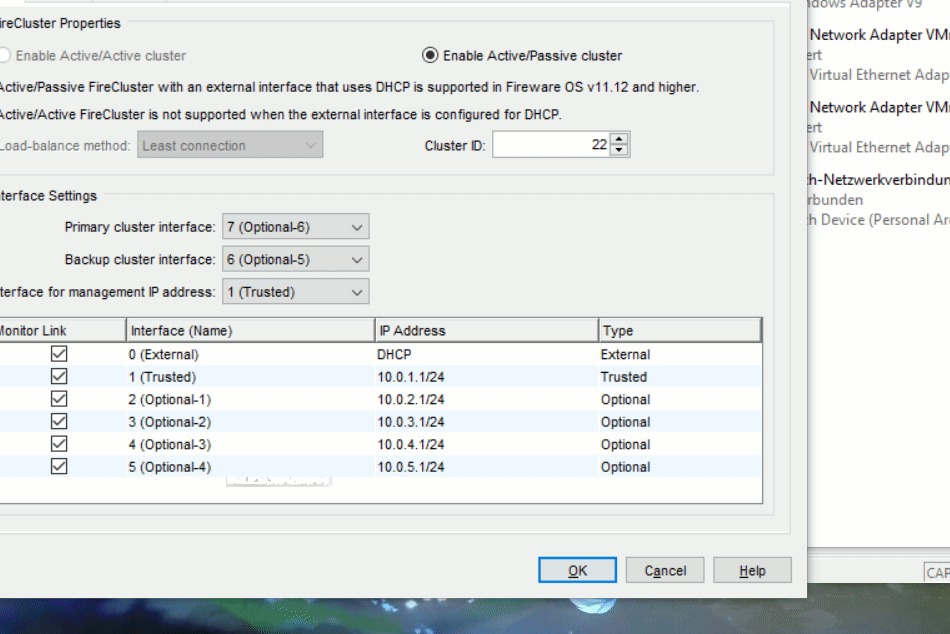
Here you select that you want to set up a active/passive cluster and use a different cluster ID then the default. On the next page you define the Cluster Interfaces, in this case 6 and 7. The Management Interface is going to be „1 (Trusted )“.
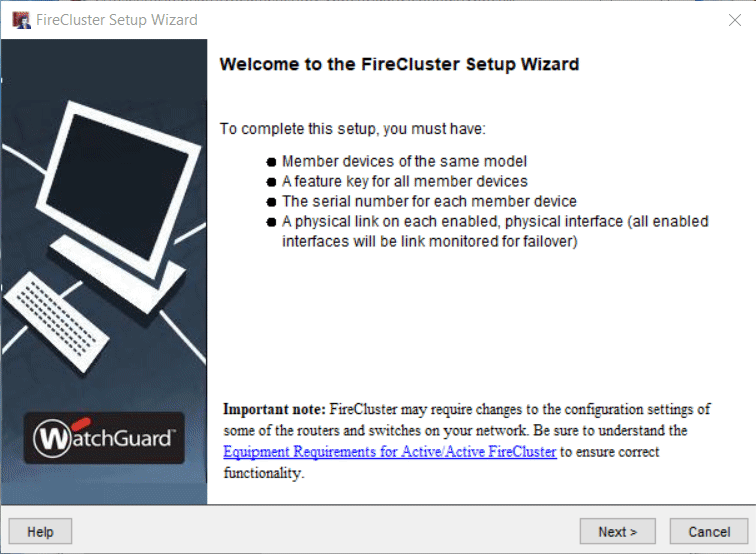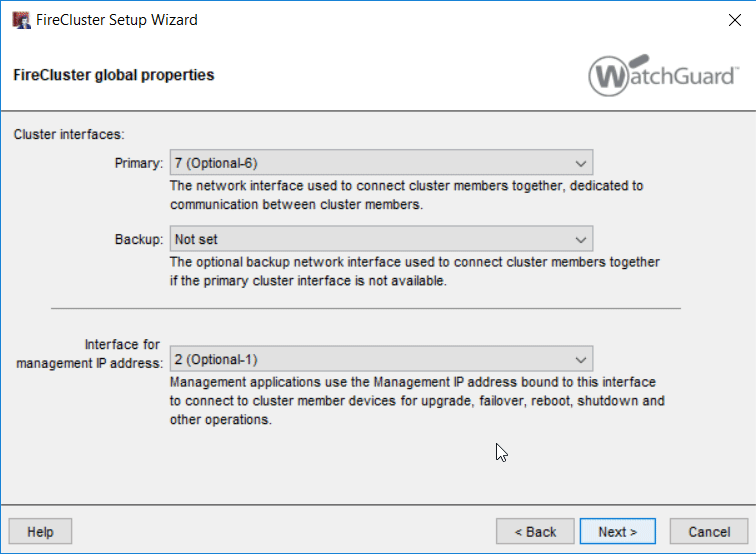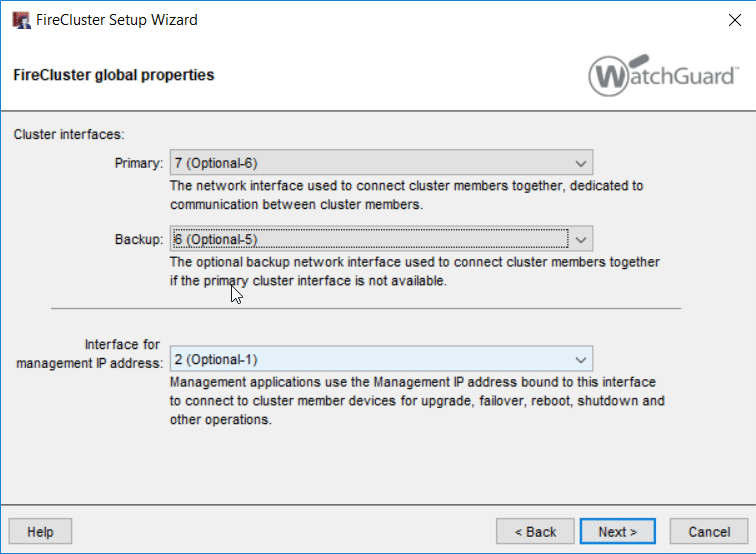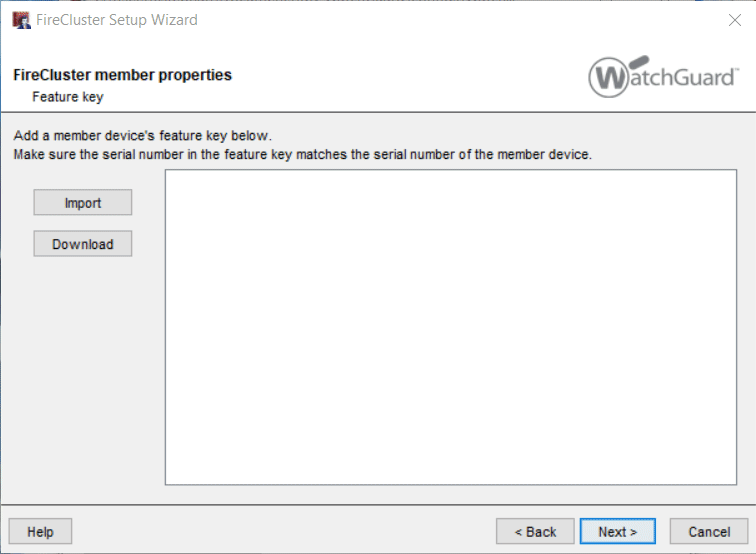
The next thing we configure is the Cluster Network and the Feature Keys einzuspielen.
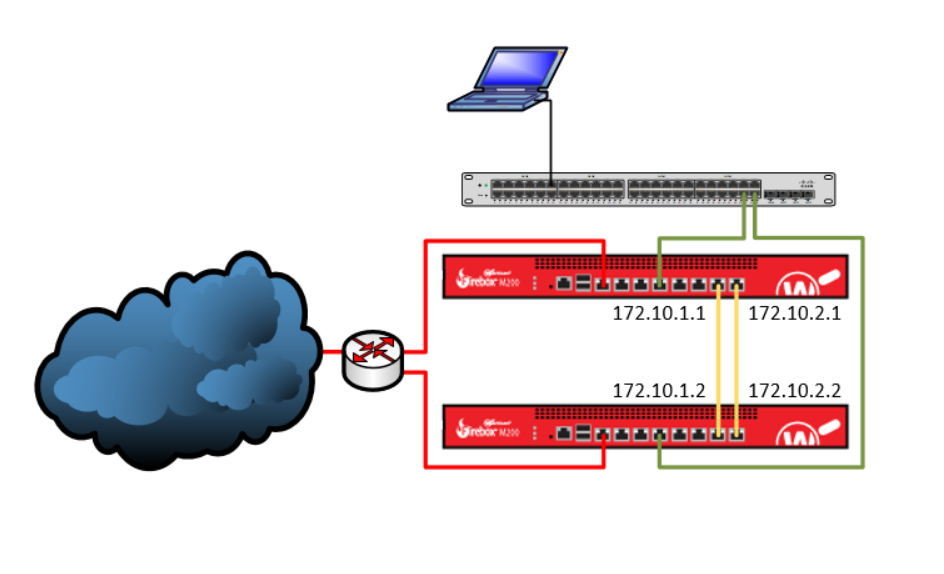
Firewall: BLN1 Management IP: 172.10.10.1 Primäres Cluster Interface: 172.10.1.1 Backup Cluster Interface: 172.10.2.1
Firewall: BLN2 Management IP: 172.10.10.2 Primäres Cluster Interface: 172.10.1.2 Backup Cluster Interface: 172.10.2.2
In the Configuration Wizard it is going to look like this:
At last we change Network > Configuration and close down Interface 1,3,4 and 5, start a DHCP range on Interface 2 and write the config to the firewall.

After rebooting the firewalls we can check if on both devices Interface 2 is providing DHCP.
Testing a Failover
We should verify that the setup is working properly. Connect to the Management IP of the cluster and send a ping to a target of your choice. If you pull the power on one of the firewalls the ping should only stop for a few seconds.
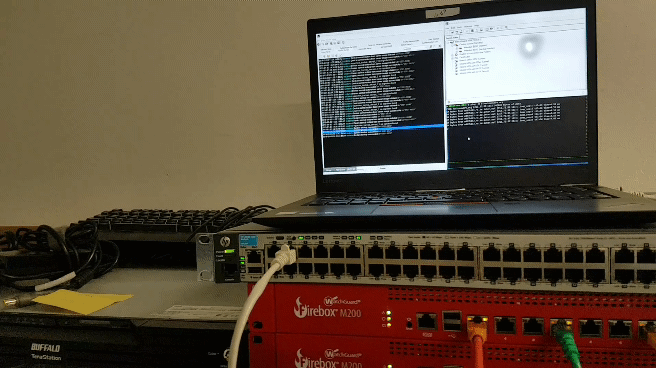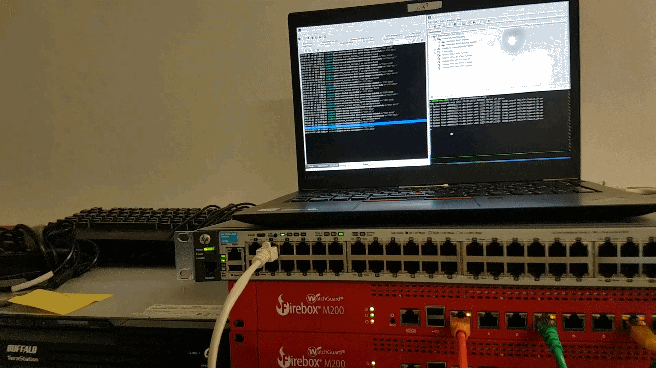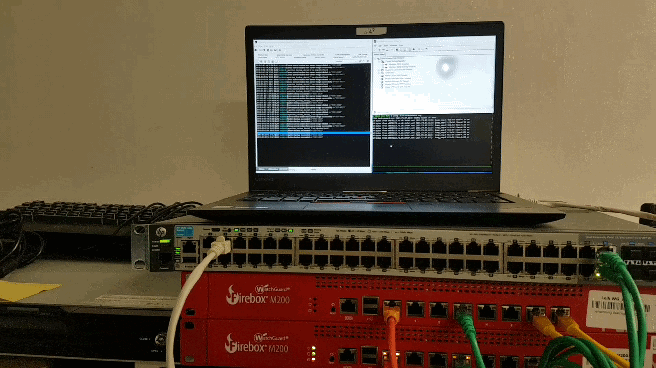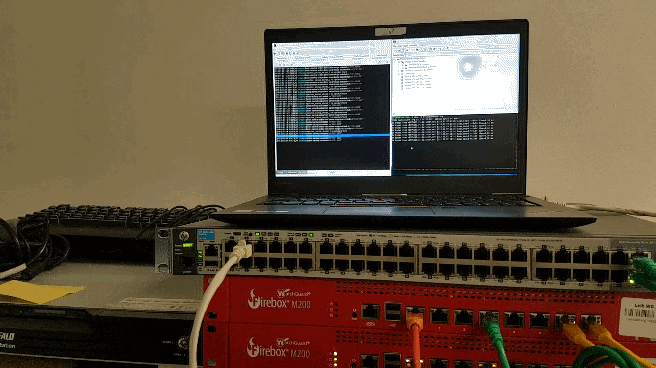
[video width=“1914” height=“1026” mp4=“https://blog.hackzenwerk.org/wp-content/uploads/2018/01/2018-01-03_15-45-07.mp4”][/video]
Cheers, Ori